The Cyber Praetorians: Dawn of the Digital Battlefield
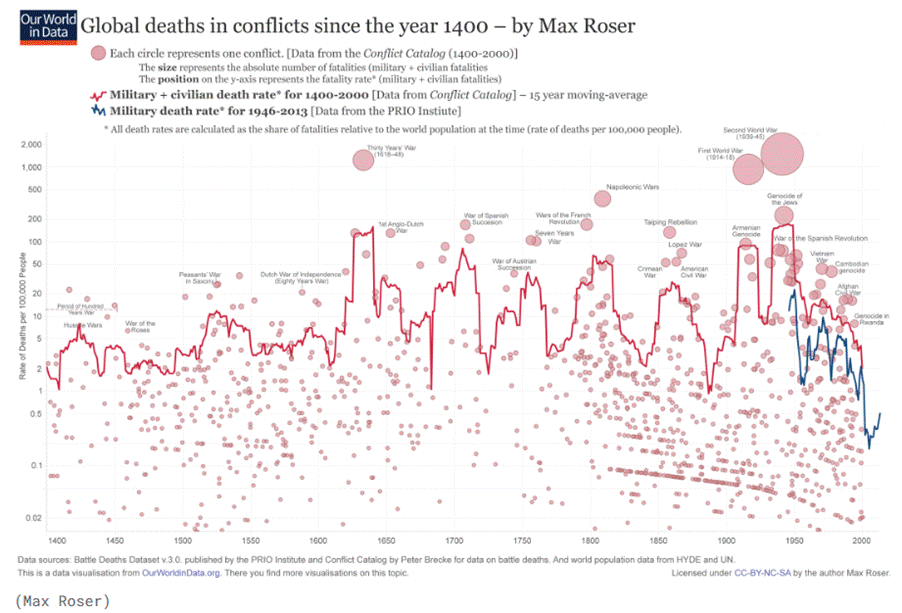
The upcoming ‘Trump’s War’, like all great wars before it, will be merely the latest chapter in humanity’s hobby of creative destruction. Once upon a time, warriors hacked at each other with swords and spears; then came castles, cavalry, and the glory of mud-soaked sieges. Gunpowder crowned kings with cannons and muskets, until industry allowed governments to perfect the art of killing at scale with tanks, planes, and chemical cocktails. The Cold War raised the stakes to nuclear annihilation while turning propaganda into a battlefield of its own.
https://www.vox.com/2015/6/23/8832311/war-casualties-600-years
Now, in 2025, the battlefield is no longer only blood-soaked earth but energy grids, satellites, and the fragile minds of the masses. Wars are not only won with bombs but also with algorithms, not with invasions but with login credentials. Cyberwarfare lets nations project power at bargain prices, cloaking their sabotage in “plausible deniability.”
In this multipolar order, no single empire rules—yet every empire must hack, spy, and disrupt to survive. Algorithms are the new artillery, networks the new trenches, and cybersecurity the new iron shield. After all, who needs tanks when you can crash a currency with a line of code?
Cybersecurity is no longer a mere IT chore—it is the digital fortress wall guarding empires, corporations, and even your grandmother’s bank account. Once limited to firewalls and passwords, it now dictates who controls economies, armies, and public opinion. From energy grids to financial systems, every network is a battlefield, and every citizen a potential liability.
The cybersecurity industry, the new Praetorian Guard, shields the realm from hackers, ransomware barons, crypto-thieves, and digital saboteurs. Its weapons—firewalls, VPNs, intrusion detection systems—are the modern equivalents of tanks and missiles. Policies and training are drilled into obedient employees like military discipline, because a single careless click can be treason. In this glorious era of connectivity, cybersecurity is not just protection—it is survival. Those who fail to defend their data shall be ruled by those who steal it.
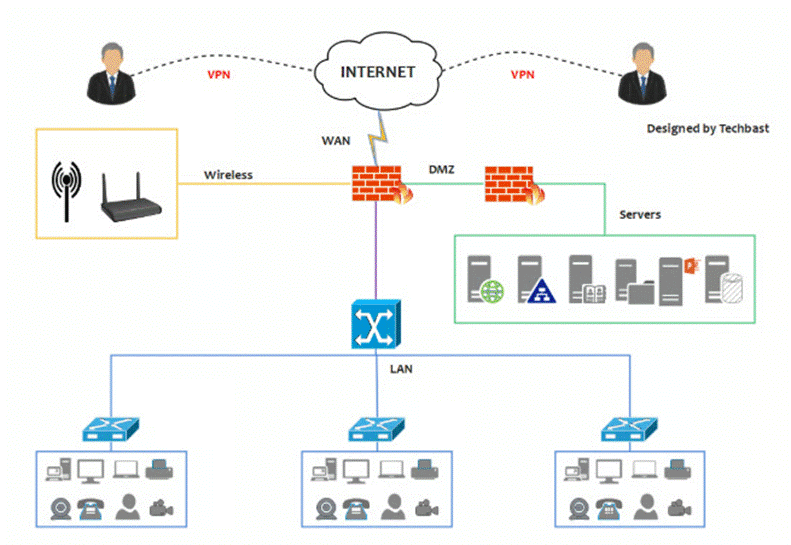
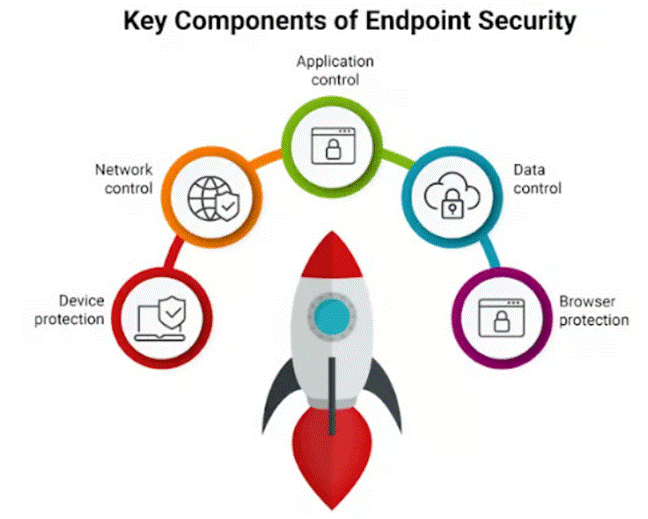
Cyber defence has become less about moats and catapults and more about digital battalions. Next-Gen Firewalls stand guard like elite sentries, armed with malware-sniffing dogs and sandbox drills. IDS/IPS units patrol the perimeter, sniffing out intruders with signature scrolls and anomaly radars. Network segmentation, the digital version of castle walls, ensures that if the barbarians breach one gate, they won’t sack the whole kingdom. The battle grows fiercer with the rise of cloud fortresses, zero-day assassins, and shadowy APT warlords—forcing armies to recruit AI scouts. And on the front lines, endpoint security shields every soldier’s laptop, phone, and server, patching wounds in real-time before the plague of ransomware sweeps the camp.
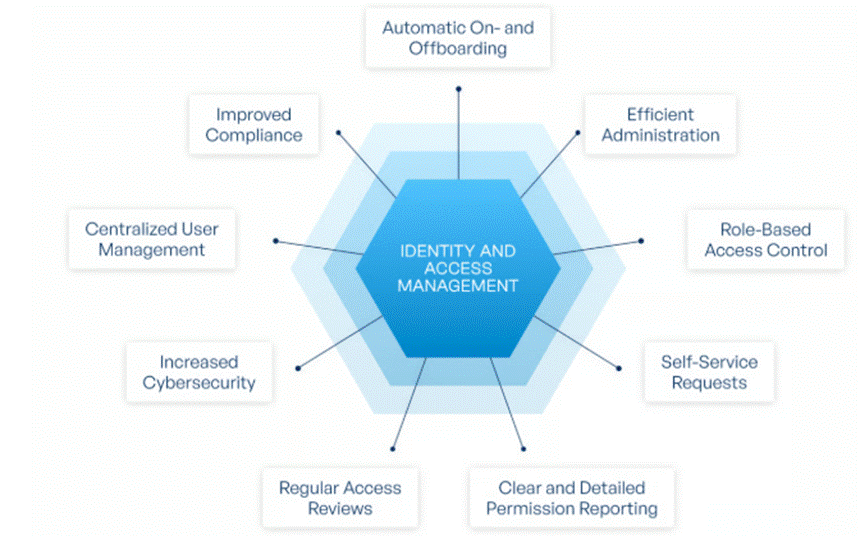
Endpoint defence is no longer just about clunky old antivirus knights swinging signature-based swords at familiar foes. The modern battlefield now calls for EDR shock troops—armed with behavioural analytics, sandbox trials, and the cunning to unmask zero-day assassins. With every worker marching into the office armed with their own device, the attack surface has grown into an open plain, ripe for ambush. Meanwhile, elusive enemies like fileless malware demand sharper detection and faster reflexes. Overseeing it all is Identity & Access Management, the gatekeeper general, deciding who gets through the fortress gates and who gets tossed into the moat.
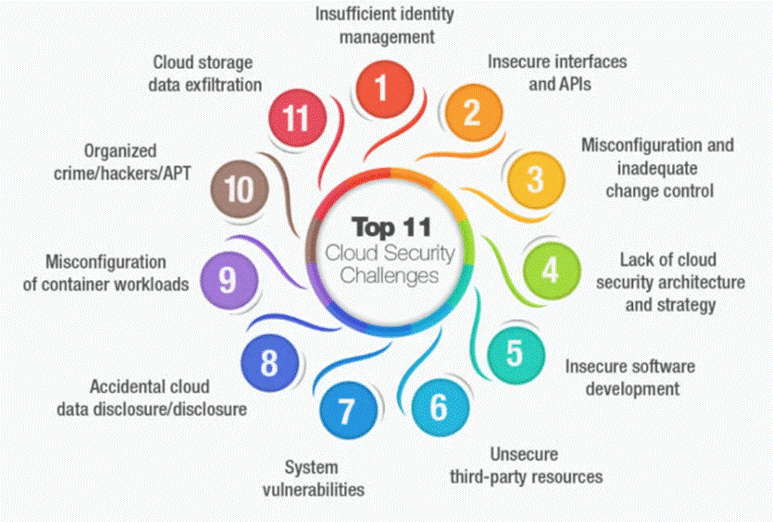
In the realm of Identity & Access Management, Single Sign-On is the skeleton key—one password to rule them all, sparing users from juggling a dozen secret codes. But since phishing armies are forever lurking, Multi-Factor Authentication stands guard like a grizzled veteran, demanding extra proof before letting anyone past the gates. With cloud empires rising and SaaS strongholds multiplying, IAM has become the indispensable gatekeeper of the digital kingdom. And as armies march their data into public and private clouds, cloud security takes command—encrypting treasures, monitoring for ambushes, and rallying incident response troops the moment an enemy slip through the mist.
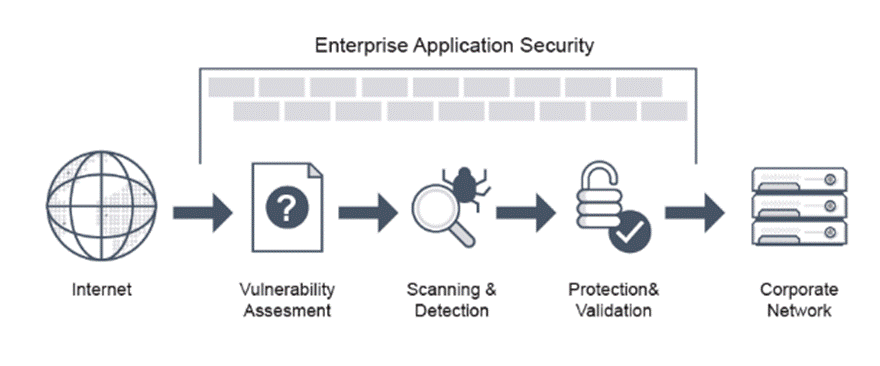
In the cloud war theatre, IaaS is the supply line—virtual machines, storage, and networks hauled in like wagons of grain—while PaaS is the weapons forge, where developers hammer out new applications under the watch of digital blacksmiths. But as public clouds swell into sprawling empires, so too does the need for hardened defences against saboteurs, spies, and insider traitors. AI scouts are now deployed to sniff out threats lurking within the ranks. On the frontlines, application security ensures that every piece of software leaves the forge battle-ready, tested, patched, and armoured against the inevitable siege of exploits and zero-day arrows.
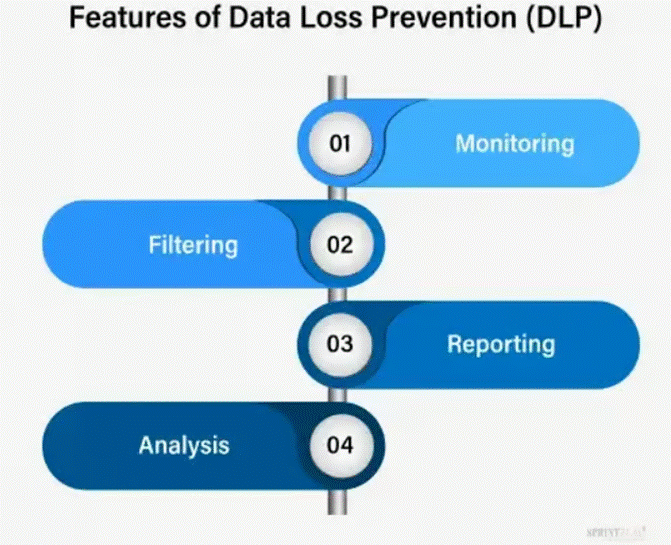
In the campaign of application security, secure coding practices are the disciplined drill sergeants, enforcing memory safety and order in the ranks of code. SAST tools act as scouts, combing through source lines to uncover weak spots before the software marches into battle. With DevOps and Agile accelerating the pace of deployment, these scouts must keep up with the charge, integrating seamlessly into the army’s maneuvers. But as supply chain attacks sneak weapons into the arsenal itself, AI-powered sentinels are being trained to spot treachery before it spreads. Meanwhile, Data Loss Prevention stands as the quartermaster of the digital army, policing the flow of sensitive information and ensuring no secrets escape the fortress walls.
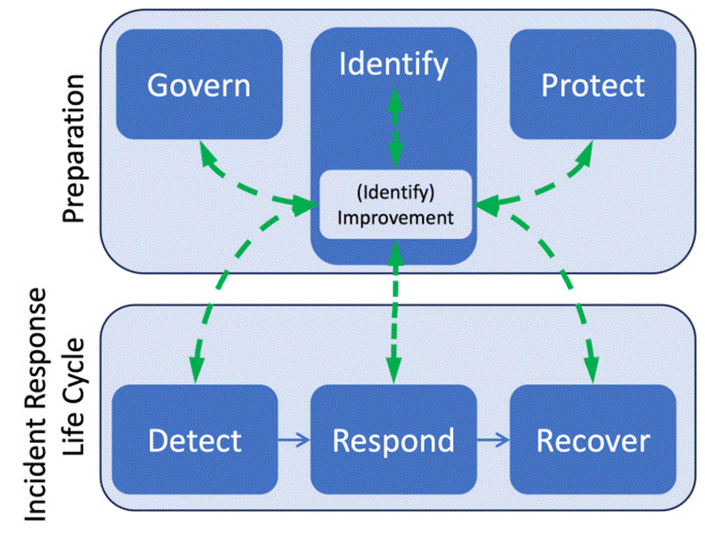
In the DLP regiment, network-based troops patrol the data highways, intercepting suspicious traffic before it slips past the gates, while endpoint-based sentinels stand watch over individual devices, catching leaks at the source. With cloud fortresses multiplying and insider traitors plotting from within, AI-powered lieutenants are being deployed to sniff out sabotage in real time. When defences fail and the enemy breaches the walls, the Incident Response division charges in—battle-hardened specialists armed with threat-hunting spears, penetration-testing battering rams, and red-team war games. Their mission: contain the chaos, patch the breach, and record every scar as a lesson for the next siege.
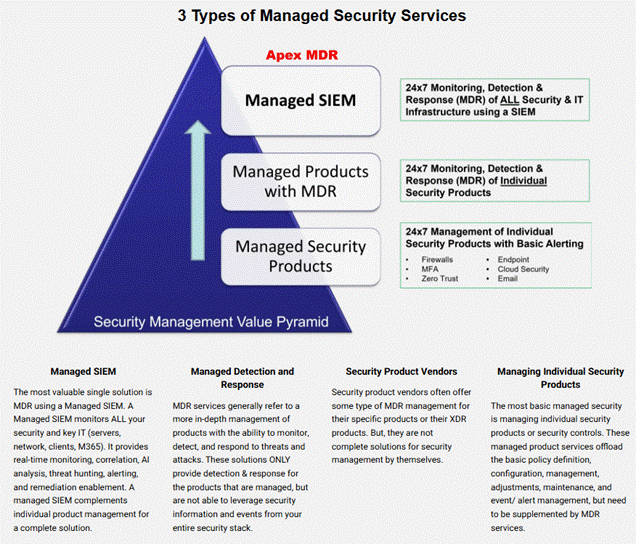
In the final echelon of the cyber army, Managed Security Services act as mercenary watchmen, patrolling networks day and night to keep threats at bay. Incident Response Planning, meanwhile, is the war manual—detailing exactly how the garrison should rally when the alarm bells sound. The battlefield has grown nastier: AI-enhanced defenses are forged to counter ever more cunning enemies, while APT warlords demand not just machines but human intelligence operatives to track their moves. Digital transformation has opened vast new fronts to defend, while regulators—from GDPR to HIPAA—march in like stern commanders, demanding compliance or punishment. And looming over all is ransomware, the digital hostage-taker, forcing kingdoms to fortify their vaults with backups and rapid-response legions.
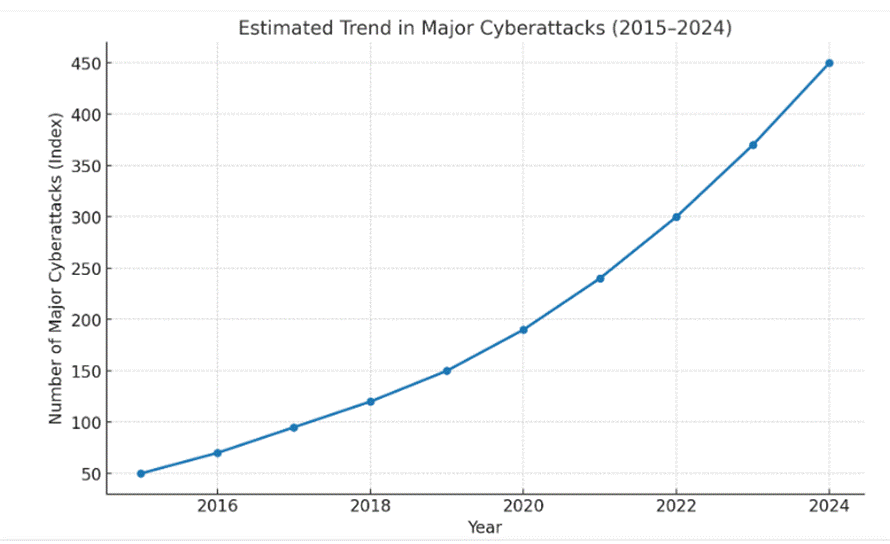
Over the past decade, cyberattacks have evolved from lone hackers poking around for quick cash into full-scale digital war campaigns waged by nation-states, crime syndicates, and activist armies. Ransomware assaults, corporate data heists, and strikes on critical infrastructure have become routine headlines, exposing just how fragile our wired world really is. The motives have broadened too—what began as financial theft has expanded into espionage, political meddling, and sabotage of global supply chains. The trend is unmistakable: cyberattacks are no longer rare ambushes but a permanent battlefield in the great game of power and profit.
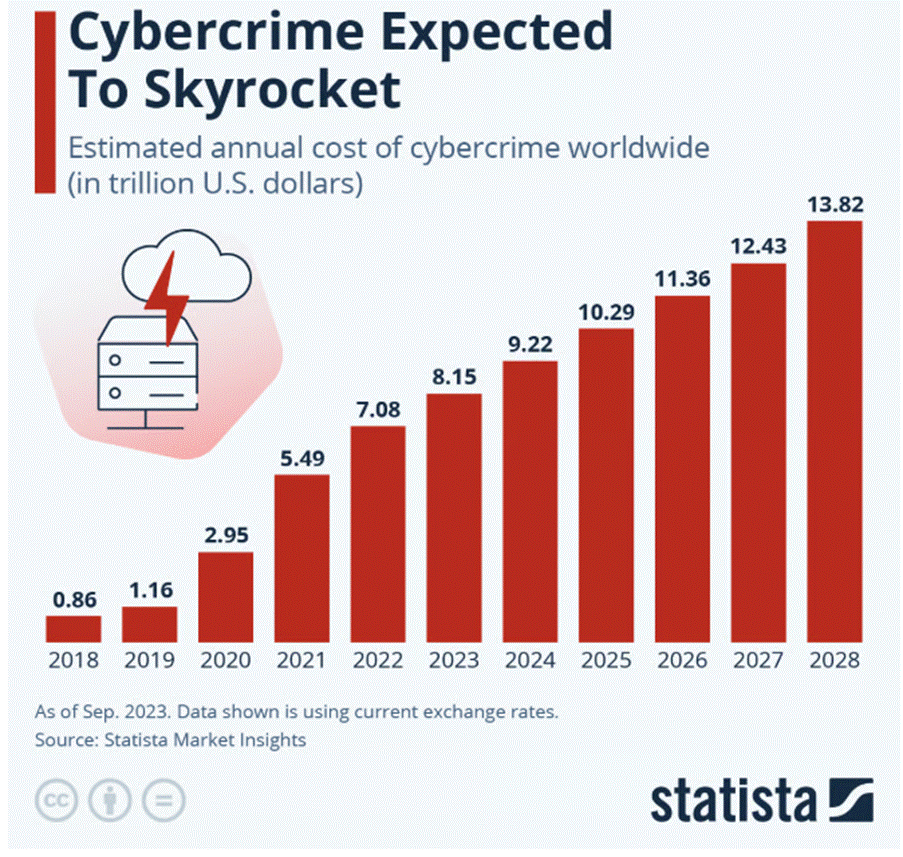
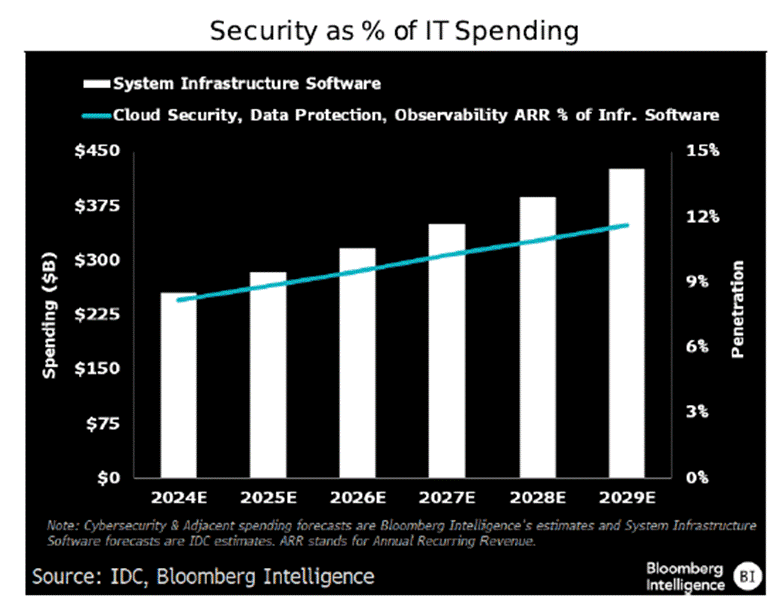
The global cybersecurity army is mustering like never before, set to seize $10.3 trillion this year, growing at over 12% annually. Fuelled by fears of data breaches, ransomware marauders, and digital saboteurs, organizations are conscripting legions of firewalls, AI scouts, and endpoint sentinels—arming every network and device to defend their treasures against the relentless onslaught of cyber invaders.
As cyberattacks surge, organizations are rallying their defences, realizing that strong cybersecurity is no longer optional—it’s the frontline trench protecting networks, data, and reputations from the relentless tide of digital invaders.
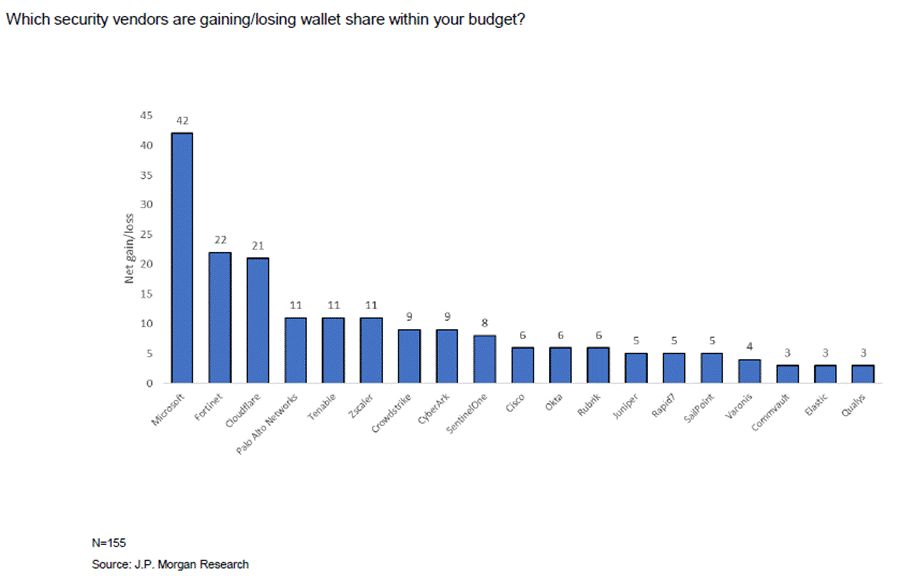
Global conflicts and cyber threats are tearing apart the once-happy marriage of cybersecurity and cloud. Cybersecurity, however, remains the overachieving child—propelled by AI, solid fundamentals, and juicy M&A prospects. Rising US-Iran tensions have fatten budgets as state-sponsored attacks pick up, though AI still drives the long-term boom. Even if Iran doesn’t spend much on IT, corporate defences will bulk up anyway: no company wants downtime, stolen data, or a headline calling them “the latest breach victim.”
AI has turned the cyber battlefield into a full-scale war zone. By 2027, 17% of attacks are expected to wield generative AI, while defenders deploy AI scouts, anomaly hunters, and autonomous strike teams in real time. Cybercriminals counter with deepfake phishing, shapeshifting malware, and 15% more attacks than last year. This is no longer a niche skirmish. AI-powered defence is now critical infrastructure, while insurgent startups with zero-trust armour and agentless tactics storm the venture capital gates. Legacy firms that fail to adapt risk being routed. For investors, the prize lies with those commanding AI-driven intelligence and autonomous response—battle-hardened troops in a war where the frontlines shift daily.
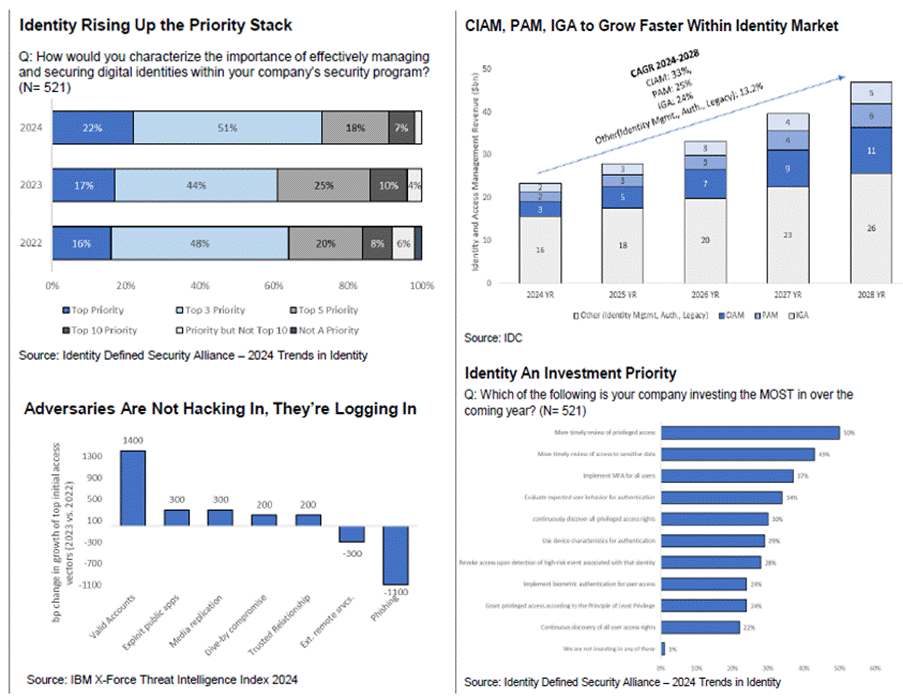
IBM’s 2024 X-Force Index reports identity attacks surged 71% year-over-year, making credentials the frontline of cyber warfare. The Identity Defined Security Alliance confirms that 22% of firms now rank digital identity as mission #1, up from 17% in 2023, while 73% place it in their top three priorities. Privileged access remains a hot growth zone, with CIAM, PAM, and IGA expected to expand 42%, 23%, and 25% in 2025. Machine identities—apps, bots, databases—now outnumber humans 45:1, according to CyberArk. In short: lock down your troops, because the enemy is already in uniform.
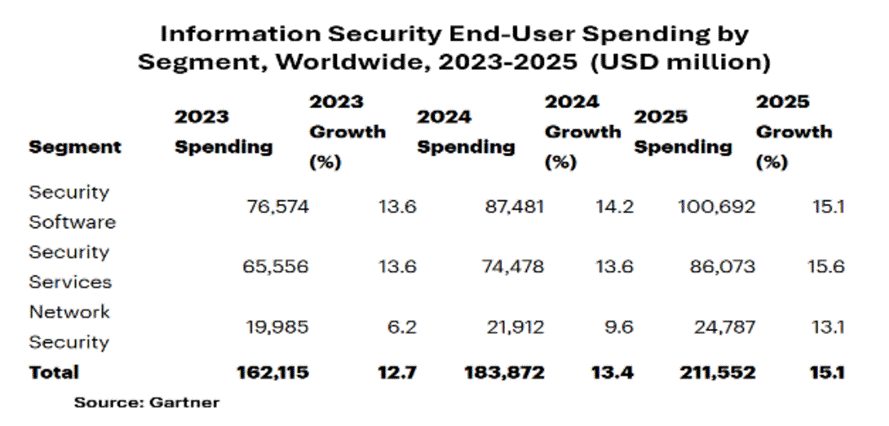
For the past 20 years, Data Loss Protection (DLP) has held the frontline, guarding data with encryption and backups, mostly on-prem. But the battlefield is evolving: DSPM is now table stakes for modern cyber armies. Acquisitions like Eureka Security by Tenable Holding (TENB), Dig Security by Palo Alto Networks (PANW), and Flow Security by CrowdStrike (CRWD) show the push to consolidate forces. Rising data volumes, new use cases, and stricter regulations are driving vendors to unify scattered defences—streamlining the fight to keep sensitive information in friendly hands.
Critical infrastructure is the backbone of society—mess with it, and the whole kingdom wobbles. At the frontlines: energy grids, transportation arteries, water supplies, hospitals, and communications. All are interlinked, but energy reigns supreme: without it, nothing else marches. Power plants, transmission lines, oil and gas networks, and control hubs are the generals and supply depots keeping the lights on. These systems face enemies from all sides: storms, sabotage, wars, and mismanagement. History reads like a battlefield report: the Russian-Ukraine war and North Stream explosion, EstLink2 cable troubles in 2024, California wildfires and rolling blackouts, Texas frozen grids in 2021, Israel’s load shedding, South Africa and Lebanon’s chronic outages. Even New York’s infamous 2003 blackout—sparked by overgrown trees touching transmission lines and a control room alarm failure—shows how small skirmishes can escalate into full-scale chaos.
Now, cyberattacks have joined the fray, targeting control systems and data centres that increasingly guzzle energy to power AI, cloud, and blockchain operations. Ireland’s data centres already consume over 20% of electricity. Governments are waking up: Switzerland now mandates reporting cyberattacks on critical infrastructure starting April 2025. The energy battlefield has never been more complex, and every outage, breach, or misstep is a lost skirmish in a high-stakes war for power and control.
The European energy battlefield is heating up—cyberattacks on grids and utilities are escalating every year. Between 2020 and 2022, 40 strikes hit European energy firms, including over 10 targeting industrial control systems. By January 2023–2024, critical infrastructure faced over 420 million attacks worldwide, with energy grids squarely in the crosshairs—a 30% yearly increase. Even small failures can trigger chaos. In June 2024, a “virtual decoupling” of Europe’s electricity market sent prices skyrocketing 3,000% when a coupling algorithm failed. In August 2024, the Netherlands’ massive solar grid—tens of millions of panels—was found vulnerable to cyber manipulation of inverters, highlighting how a coordinated attack could blackout entire regions. Offshore wind farms are under siege too, with cyberattack attempts up ten- to twenty-fold since the Ukraine war began.
Why so vulnerable? Three words: digitization, decentralization, and complexity.
Read more and discover how to trade it here: https://themacrobutler.substack.com/p/the-cyber-praetorians-dawn-of-the
Join The Macro Butler on Telegram here : https://t.me/TheMacroButlerSubstack
You can contact The Macro Butler at info@themacrobutler.com
If this research has inspired you to invest in gold and silver, consider GoldSilver.com to buy your physical gold:
https://goldsilver.com/?aff=TMB

Disclaimer
The content provided in this newsletter is for general information purposes only. No information, materials, services, and other content provided in this post constitute solicitation, recommendation, endorsement or any financial, investment, or other advice.
Seek independent professional consultation in the form of legal, financial, and fiscal advice before making any investment decisions.
Always perform your own due diligence.